It's known that the system of mobile connection, as well as internet are open (unsafe) systems, in that sense that interception, message modification or sending false messages etc. are accessible to the average hacker, not saying about full access to the information from the side of internet providers or mobile communication.
However, functionality extension of mobile communication services requires security intensification. For example, you want to send an SMS message, content of which will be available to the recipient only; or you would like to get information on your account state (operations, account balance etc.) or even you want to make active operations on your account management.
Mode №3. Signing the message on the Private Key of the sender and encryption on the Public Key of the receiver (CMS - Cryptographic Message Syntax).
Application Demo version (given below) does not contain additional screen forms, which are used in bank applications.
The application is realized on Java™ 2 Platform Micro Edition (J2ME) as MIDP application (MIDlet) for Nokia Series 40. Localization for 2 languages - Russian, English - (language choice is automatic depending on the language installed in the mobile phone).
The following basic cryptographic algorithms and standards are realized:
Encryption: MD2 (40 bit), DES (64 bit), 3DES (128/192 bit), AES (128/192/256 bit), GOST 28147 (256 bit). Basic algorithm AES (256 bit).
Digital signature: RSA (1024 - 4096 bit), GOST 34.310 (512 bit). Basic algorithm is RSA.
Hash functions: SHA1 (160 bit), SHA2 (224/ 256/384/512 bit), GOST 34.311 (256 bit). Basic hash algorithm for digital signature is SHA1. Basic algorithm in PBE encryption is SHA2 (256 bit).
For operating with the certificates и.509 the following crypto standards RSA Laboratories are realized:
PKCS#5: Password-Based Encryption Standard;
PKCS #8: Private-Key Information Syntax Standard;
PKCS#12 v1.0: Personal Information Exchange Syntax.
Mobile phones minimal requirements (can be found in the device technical characteristics):
Mode №1. (Password-Based Encryption). As minimum, the following functions should be supported by the mobile device:
Developer Platform: Series 40 2nd Edition
Java Technology::
CLDC 1.1
Wireless Messaging API (JSR-120)
MIDP 2.0
Memory:
Max JAR Size: 50 KB (no less)
Sample devices:
Nokia 6230 (http://www.forum.nokia.com/main/0,,018-2062,00.html?model=6230),
Nokia 6230i (http://www.forum.nokia.com/main/0,,018-2435,00.html?model=6230i),
and others.
Mode №2 and Mode №3. (Certificate-Based Protection).
As minimum, the following functions should be supported by the mobile device:
Developer Platform: Series 40 2nd Edition
Java Technology:
CLDC 1.1
Wireless Messaging API (JSR-120)
FileConnection and PIM API (JSR-75)
MIDP 2.0
Memory:
Max JAR Size: 200 KB (не менее)
Sample devices:
Nokia 6255 (http://www.forum.nokia.com/main/0,,018-2627,00.html?model=6255),
Nokia 5140i, 6060, 6101, 6111, 6270, 6630, 7360, 7370,
and others.
Loading the programme into the mobile device:
It is carried out by the authorized tools of mobile devices. For example, for Nokia, the application Nokia PC Suite 6.5.10 is used (supplied on the CD), Nokia Application Installer. In the left window of the Nokia Application Installer you need to choose where the application SecureSMS.jar is copied from (it is a file of this application) and by pressing the arrow (in the centre of the screen) to copy SecureSMS.jar into the mobile telephone:
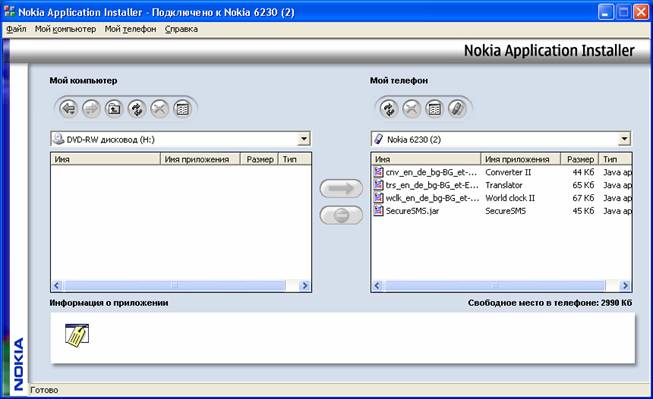

Now the application SecureSMS can be started from the mobile.s menu "Applications".
If you want to work with the certificates, it is essential to follow these steps:
1. Using your PC (or a provider.s) to generate a Private Key of the digital signature and get a digital certificate.
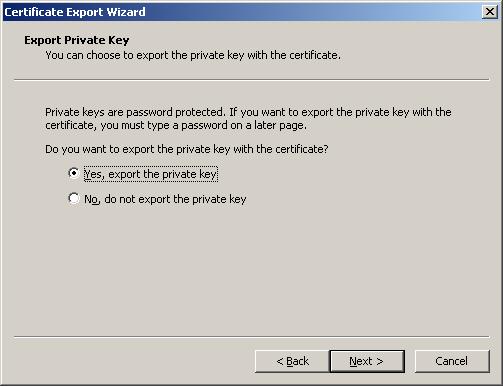
2. Unload the key and the certificate into the file main.pfx . open the browser Microsoft Internet Explorer/Service/Browser properties: / content/ certificates: choose the certificate which you need to unload and perform "Export:". At the same time, to indicate "Yes, export the private key":
Then choose "As far as possible include all the certificates into the certificate path":
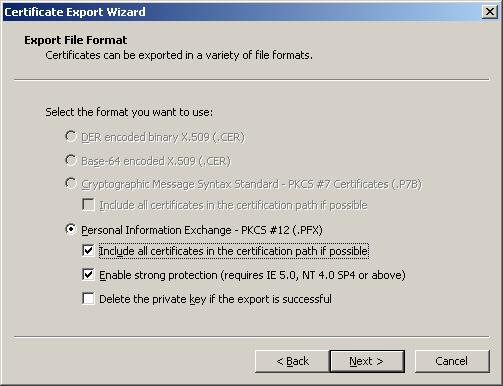
Complete the export into the file with the name.
3. Connect the mobile device to the computer. Choose "File dispatcher" in the tools menu (Nokia PC Suite 6.5.10).
Note. You can make all steps with the Windows Explorer.
On the memory card (е) of the mobile device create a folder and copy the file of the key "main.pfx" into it (which you got on the previous step). You can additionally create the folders "smsinbox" (for inbox SMS), "smsoutbox" (for sent SMS), (for saved SMS messages). Information on what these files are meant for is mentioned below.
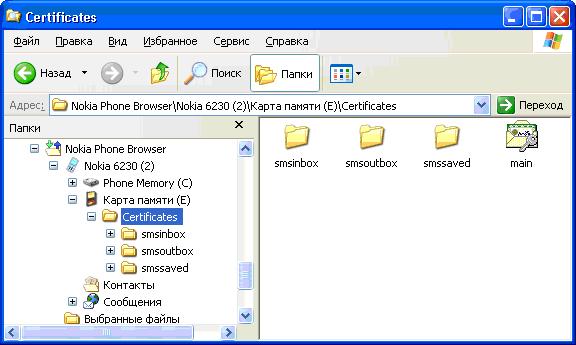
At this point the preparation work is over. You can disconnect the device from the computer and operate with the mobile device itself. Now the application SecureSMS can be started from the menu "Applications" of the mobile phone.
Operating with the application secureSMS
When starting the application, the workability with the certificates is checked, viz:
1. It is checked that a mobile supports the essential Java Technologies (see above).
2. It is checked that there is a folder "Certificates" on the Memory card (е) in the mobile device and there is a key file "main.pfx" in it.
When starting the application for the first time, the certificate repository file "certs.amb" has not been created yet in the folder "Certificates", thus it is possible to use the mode N1 only (password-based encryption).
Main menu of the application
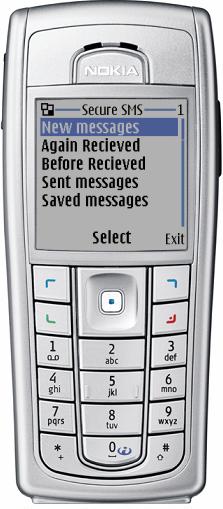
The main menu of the application contains the following items:
New message - for creating and sending messages;
Inbox - for reading the inbox messages;
Sent - for reading the sent messages;
Saved - for reading and sending the saved messages.
In the folders "smsinbox" and "smsoutbox" only those messages can be written which are signed with the digital signature. Saving these messages can be required for demonstration that the signed message (or an e-document) has been sent or received.
Messages which have been encrypted but have not been signed with the digital signature are not saved.
The Folder "smssaved" is designed for writing into it the message files, which have been created on the PC, and their further sending by the application SecureSMS. This can be used for speeding-up the process of writing the documents or in case of larger documents (see below).
Screen "New message" (mode Password-based-Encryption)
As it was mentioned above, when starting the application for the first time, the certificate repository file "certs.amb" has not been created yet in the folder "Certificates", thus it is possible to use the mode .1 only (password-based encryption). Enter the screen of the message, which is being encrypted on the password.
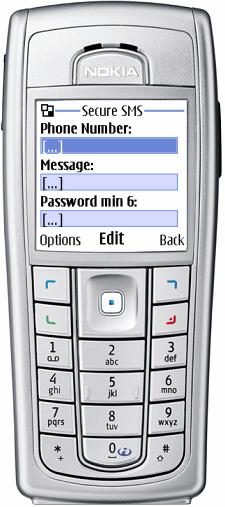
Enter the data into the fields (in every field choose the command "Change").
The field "Telephone number" can be filled out directly with the menu (button) "Options"/"Search" -
choose the needed number from the phone address book. A number can start with (or without) <+> and contain the digits only.
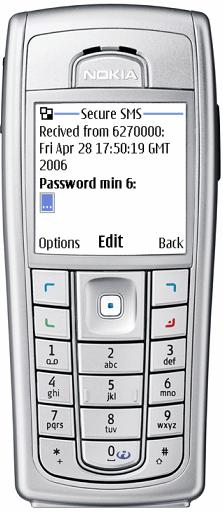
The fields "Message" and "Password:" are entered directly from the phone keypad. The password is not shown on the screen. The password should contain no less than 6 symbols (any), the message is encrypted with it. To decrypt this message you need to enter the same password (see below the Receiving messages Mode).
After all the data have been entered, the command "Change" in the fields "Message" and "Password:" is changed onto the command "Send message" and you can send a message.
If some fields are not entered, the message can not be sent, and you will be notified of the error with an empty field indicated.
After the message has been sent, the screen stays filled in. You can send the same message to another addressee.
Transition to the mode №2 "Certificate-based Encryption"
Screen "New message" contains an extra menu in the list "Options" (left button).
When choosing "Options", the extra command menu appears:

|
Send message
Read certificate
Certificate-encryption
Password-encryption
Sign&Encrypt
Certificates List
Send certificate
|
As it was mentioned above, when starting the application for the first time, the certificate repository file "certs.amb" has not been created yet in the folder "Certificates". If you have a personal key in this folder (file main.pfx), in this case choose the menu .Certificate-encryption.. The application will start creating the certificate repository file certs.amb. The application will ask for the key file main.pfx password and will automatically create the certificate repository file certs.amb, where your certificate will be placed from the key file main.pfx. If the password is wrong or the file main.pfx integrity has been violated, in this case you will be notified of the error. The certificate repository integrity is protected upon the standard PKCS#12 in the public-key integrity mode.
The certificate is given a name "My" (it is prohibited to change this name), if the registration is carried out with the names, or it is given a number "0" (naught), if the registration is carried out with the telephone numbers. If for a trial you want to send an encrypted message to your own number, you have to give your real phone number (see below the command "Certificate List")
Note.
Reading the file main.pfx, checking its integrity, decryption and creating the repository file require some time (it depends on the mobile make), so you need to wait.
Screen "New message" (mode Certification - Encryption)
When the certificate repository file is created successfully, you can work in the modes 2 and 3. In the screen "New message" the field "Certification" will be placed instead of "Password"..
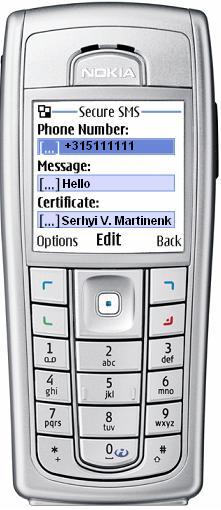
With the further re-starts of the program, integrity of the certificate repository file is checked and if it is successful, the screen "New message" (Certificate-Encryption) is installed on default.
The transition to the mode "Password-Encryption" or other modes is possible with the additional menu of the screen "New message" by choosing one of the points:
Certificate-encryption
Password-encryption
Sign&Encrypt
Certificates List
Send certificate
As in the previous case, the telephone number may be dialed using the telephone keypad or the menu .Search. from the address book.
The application checks the availability of a demanding certificate connected with pointed addressee (number) in the certificate repository and shows the owner/subject name in the field "Certificate" or "No certificate", if there is no certificate. If there is no certificate, it is impossible to send a message in this mode - choose the mode 1 Password - Encryption. The telephone number and the message text are saved when changing the mode.
Screen "New message" (mode Sign&Encrypt)
"Sign&Encrypt" mode is assigned for message sending, signed on your Private Key and encrypted on the addressee's Public Key (certificate).
If you have a Private Key main.pfx for signing a message and there is an addressee's certificate in the certificate repository, in this case you may choose the mode "Sign&Encrypt" in the additional screen menu "New message".
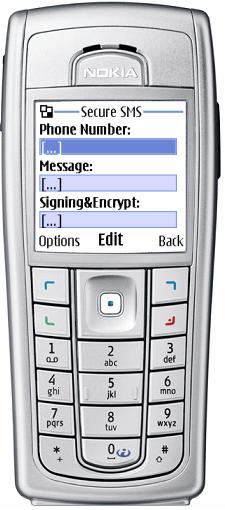
The mode announcement: "Sign&Encrypt" is shown instead of the field name "Certificate", however, the certificate owner/subject name is shown in this field, or "No certificate" if there is no certificate.
The data entering rules are the same as in the previous mode.
Screen "New message" (mode Send Certificate)
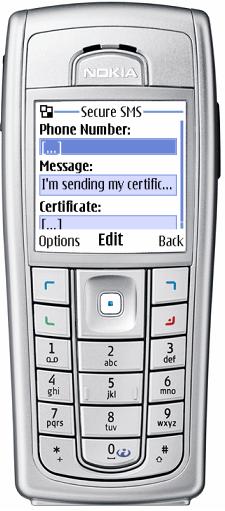
Your user can encrypt the messages in your address on your certificate, if your certificate will be in his certificate repository. Your certificate can be transferred in the mode "Send Certificate" (in the additional screen menu "New message"). To display this mode in the field "Message", the message text "I send my certificate" appears automatically.
The field can be edited, so you can supplement this message with your own text.
Note.
When receiving such a message, availability of the attached certificate is defined automatically, that is why the standard text of the message can be supplemented / changed.
Screen "New message" (command "Review the certificate")
After you have chosen a user's number in one of the operating modes with the certificates, and the field of the certificate has displayed information on the certificate owner, you can read more detailed information on the certificate. You can do this by choosing "Review the certificate" in the additional screen menu "New message".
Screen "New message" (command "The list of certificates")
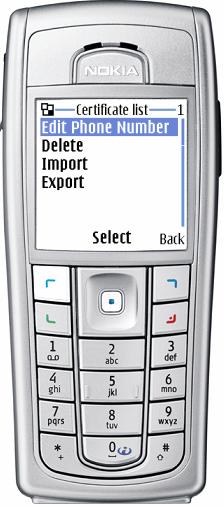
To see the list of certificates, which are in the certificate repository, choose "List of certificates" in the additional screen menu "New message".
The list can be shown with the telephone numbers or users' names.
To review the certificate you need to press the button "Choose".
The screen .List of certificates. has the additional menu (commands):
Change the number
Delete the number
Import
Export
Command "Change the number" allows editing the number or choosing from the address book via the additional menu "Search".
Note.
Command "Delete the number" is followed by the inquiry on removal confirmation. You should be careful about deleting the certificate, as the certificate is deleted from the repository, but there is no command "Undo removal".

Report screens
Report screens are formed in the following cases:
When the message is sent the screen "Report" is formed, where you can see information on the encryption algorithm and the sending mode (command "Details").
In the mode "Password-based-encryption" the message authentication code (MAC) is shown in the screen "Details". In the operating modes with the certificates there is additional information on the encryption certificate or on the transmitted certificate (user.s name, issuer.s name, serial number etc.).
In the receiving mode
a decrypted message can be seen on the main screen, on the screen "Details" you can find the same information as in the sending mode.
Note. If in the mobile device English language is chosen, but the incoming data are in Cyrillic (Russian) or any other language except for the English, in this case instead of the text on the screen you will see the signs .?????.. The same can me said about information in the certificate (see the example of the screen).
In conclusion, above you can find the description of the application, which ensures secure SMS. The application can be easily adapted for M-banking by adding some screens on receiving/sending standard messages. In a similar way the application can be adapted for MMS, http etc.

